![]() Learn web security threats challenges and solutions. Security attack possibilities, position of SSL in transport layers etc.
Learn web security threats challenges and solutions. Security attack possibilities, position of SSL in transport layers etc.
1. Overview of Security Threats Challenges and Solutions
This post is about, different web security threats , challenges and its solutions.
Usually, we use HTTP protocol in the web for transport layer but recommended is HTTPS (HTTP over SSL). One question comes to your mind, Why you required HTTP over SSL?
The answer is very simple, for securing your data over the transport layer while traversing. Now next questions can come to your mind what sort of security you expect by enabling HTTP over SSL. HTTPS enables transport-level security between client and server. It means, no one can intercept plain text data over the transport level if you send it an encrypted version. It means the Client sends encrypted data to Server and the server received the data and then decrypts it before the process. Once processing is done then again server sends back encrypted data in response to the client over the network that is what HTTPS works. Of course, there are multiple steps (communication done between client and server, I will try to explain in another post.
You can visit about overview of SSL protocol
2. What are the Web security Threats
- identity theft
- loss of confidential information
- theft of network resources
- damage of brand or reputation
- loss of confidence of customer etc..
Security does not comes free to you, of course you have to pay somewhere, meaning that you have to compromise with performance and cost. As I know the thumb rule , there is no free lunch in the world. Let us understand, basic building block of security threats step by step. So, there is trade-off between security and performance, that you have to balance as per your context.
3. Scenario of Security Attacks
Let us consider a web application hosted on a server and no HTTPS ( HTTP over SSL ) enabled for the application. An a end-user e.g. Bob is surfing the Web and arrives at the shopping cart application, web site, which is selling goods. For simplicity, I take a single form, let us consider a single form, shopping site displays a form in which Bob is supposed to enter the type of item and quantity, his address, and his payment card number. Bob enters this information, clicks on submit, and expects to receive the goods.
Once Bob submitted, form information flow from client to server via HTTP protocol, assuming no SSL enable. What happened?
4. Security Attack Possibilities
There could be a chances of any of the possible security attacks. These are the common day-to-day scenarios. The question is, how can we over come these scenarios. Let us first understand the different security Attack then, thinking of overcome will be simpler for you.
- Attack on Confidentiality: If no confidentiality (encryption) is used, an intruder could intercept Bob’s order and obtain his payment card information. The intruder could then make purchases at Bob’s expense.
- Attack on Integrity: If no data integrity is used, an intruder could modify Bob’s order, having him purchase ten times more items than desired.
- Attack on Availability: A competitor can flood bogus requests to bring shopping car Application (let say A2Z shopping Inc) web server down.
- Attack on Authenticity: If no server authentication is used, a fake server could display shopping car Application (A2Z shopping) famous logo when in actuality the site is maintained by crooks, who are masquerading as A2Z shopping.
The above example is related to Web application that uses HTTP, but a similar situation can occur in any type of application that uses TCP/UDP transport service.
Binding security to the specific application (browser) is not a good idea. How can we achieve security with application independence? At least up to some extent, we need to think on this as architects to achieve non-functional requirements like this.
5. Solution of Web Security
One of the solutions is to enable SSL (Secure Socket Layer) on the transport layer as security i.e. HTTPS (HTTP over SSL).
First of all, let us understand the purpose of SSL. Its purpose of SSL is to enhance the capability of TCP with confidentiality, data integrity, server authentication, and client authentication features to protect from the security threats discussed in this post.
It was developed by Dr. Taher ElGamal, present security CTO of salesforce.com during his Netscape tenure during 1995-98.
SSL is often used to provide security to transactions that take place over HTTP. However, because SSL secures TCP, it can be employed by any application that runs over TCP. Security having application independence is the prime motivation behind SSL, meaning that, for enable SSL , application is independent, no change is the application level to enable SSL for any application.
SSL provides a simple Application Programmer Interface (API) with sockets, which is similar and analogous to TCP’s API. When an application wants to employ SSL, the application includes SSL classes/libraries.
SSL follow-on standard known as Transport Layer Security (TLS) is defined in IETF RFC-5246.
We will discuss about SSL in more details in next post.
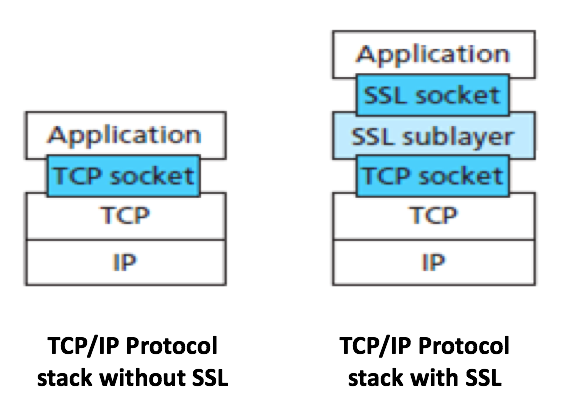
6. Position of SSL in Transport layer
7. Reference
In the left you can see no SSL enable in the HTTPS and in the right you can see SSL enable in the right.
The design of SSL subLayers allows application independence. Application layer can directly interact with the SSL Socket layer once connection established between client an server.
I hope you enjoyed this post of Web security threats, challenges and solutions, and you can visit tutorials index page for more blog post. You can visit Security Objectives
Your comments are welcome to improve this post. Happy Learning 🙂
good one
Thank you so much for sharing a great article. Keep up the great work!
Very good info. Lucky me I recently found your website by chance
I’ve book marked it for later!
thank you for all your efforts that you have put in this.
Very interesting information.