 Learn 4 phases of SSL protocol and its phases. SSL: Secure Socket Layer is handshake protocol, SSL is record protocol. Learn how it works internally before start sending data over the transport layer from the application layer.
Learn 4 phases of SSL protocol and its phases. SSL: Secure Socket Layer is handshake protocol, SSL is record protocol. Learn how it works internally before start sending data over the transport layer from the application layer.
1. Overview of 4 Phases of SSL Handshake
In this article, you learn all the 4 phases of SSL protocol and its phases in detail which include, the architecture of SSL, SSL record protocol steps, all 4 phases. If you are a novice in SSL and you have not gone through my previous article on SSL protocol overview, you must visit before this article, which is a basic building block of SSL (Secure Socket Layer) protocol.
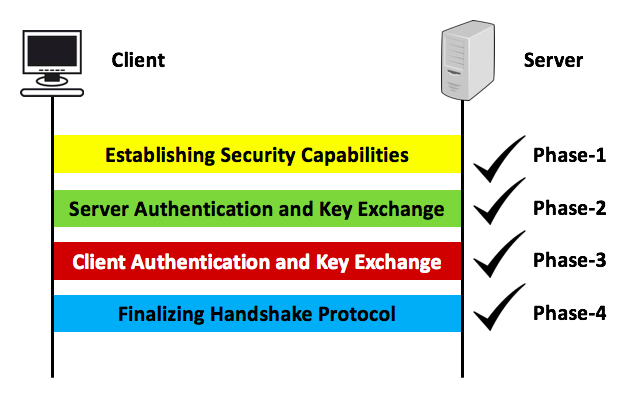
4 phases of SSL protocol are as follows:
- Phase-1: Establishing Securing Capabilities
- Phase-2: Server Authentication and Key Exchange
- Phase-3: Client Authentication and Key Exchange
- Phase-4: Finalizing Handshake Protocol
All these phases are showcased in this article with graphical view step by step which gives you more insight about SSLL handshake protocol. In this image, one client is trying to connect into remote system/machine by using SSL (Secure Socket Layer). SSL is basically used over transport layer with HTTP protocol. HTTPs has been included in this article, so for few minuts forgot about HTTPS and learn how SSL works internally.
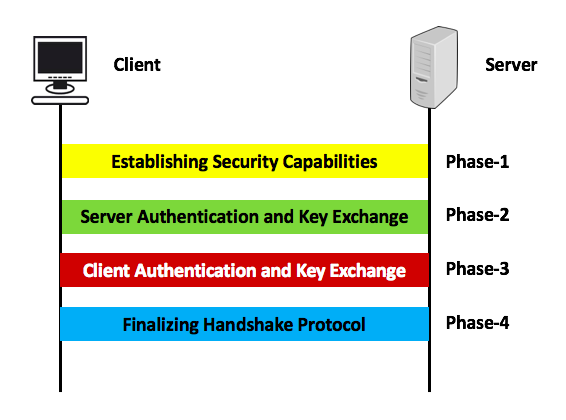
Let us understand one by one of each phase of SSL protocol in details , about how it works.
2. Phase-1: Establishing Securing Capabilities
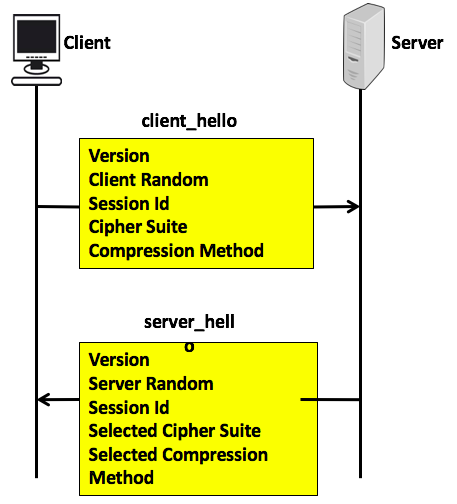
In the first phase, you learn about establishing security capabilities which is used to exchange security capabilities and satarted by client_hello message sent by the client to the server and server_hello message sent by server to the clinet. It contains various parameters:
2.1 client_hello:
- version:
- client random : 32 bits timestamp + 28 bytes of random generated by client
- session Id: variable session length, 0 mean new session, else client want to update existing session.
- cipher Suite : list of the course for decreasing order like keys, encryption methodology, etc..
- compression Method: method which used for compression etc.
2.2 server_hello
- version: either send by client or server version if
- server random: similar type of client session but independent of client.
- session Id: if client id is 0 server put new session id which indicates new session else client id
- selected Cipher Suite: selected suites by client
- selected compression method: selected compression algorithm used in during transfer.
3. Phase-2: Server Authentication and Key Exchange
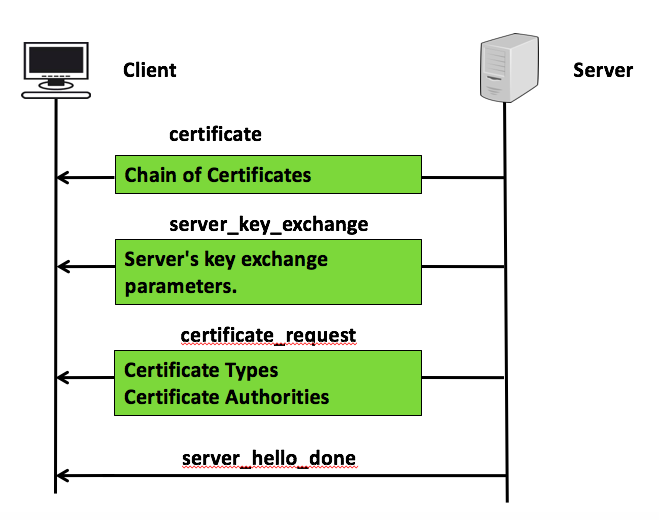
In phase-2, you learn about how SSL Handshake protocol authentication and exchange its key. This phase 2 is used by server to send following message to the client.
- Certificate: this message conveys server certificate to the client.
- server_key_exchange: this is sent by server only when server certificate does not contains enough data to allow the client master pre secret. it contains server’s key exchange parameters
- certificate_request: server request certificate from the client , it has two things: certificates types which contains list of certificate types that client may offer and list of certificate authorities , as list of distinguise name of acceptable certificate authorities.
- server_hello_done: send message sent by serve to indicate and done with key exchange and client can proceed with this phase exchange. there is no any parameter with this message.
4. Phase-3: Client Authentication and Key Exchange
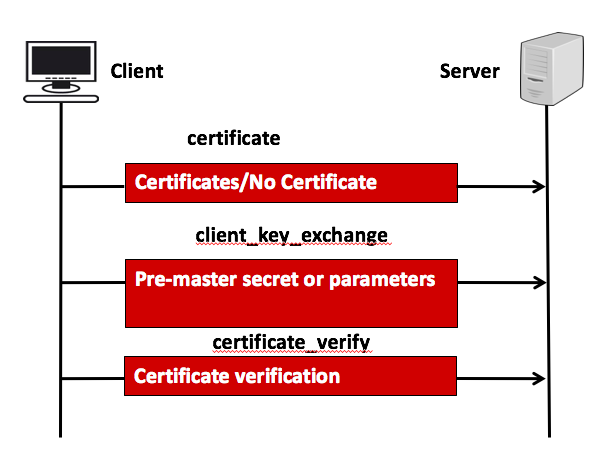
This phase 3 used by the client to send the following message to the server.
- certificates: this message is send to if not suitable certificate is available , if some aspect change unexpectedly
- client_key_exchange: depending on the cipher suit selector on phase-1, with this message either pre master secret and parametrs sent which is used to calculate both side,
- certificate_verify: use to provide explicit verification of client certificate. it must immediately follows client_key_exchange.
5. Phase-4: Finalizing Handshake Protocol
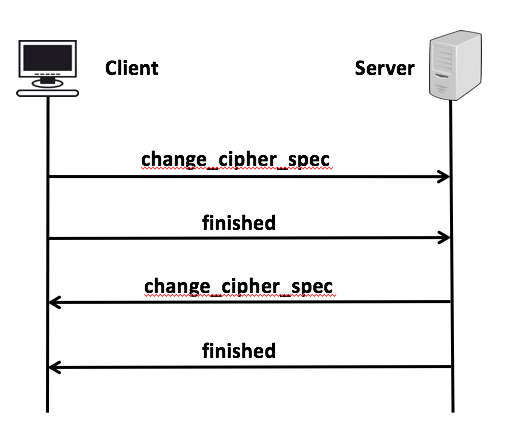
6. SSL Protocol: Finally SSL Handshake
All 4 phases of the SSL handshake protocol perform their functionalities and move to the next step.
Once the session has been established then the SSL record protocol starts sending data which has been explained in the previous post of SSL protocol overview. It is the only session that enables multiple connections. In SSL protocol too, there is a session and there is a connection. for the session, there could be multiple connections.
The session is created by the SSL protocol. The session is identified by cryptographic parameters. A session parameters can be used across multiple connections to avoid time-consuming new security parameters.
A connection is a peer-to-peer relationship. e.g. a client can exchange application data with a server so that there is a connection. The connection is transient and associated with the session.
There are some parameters which is associated with the session and some parameter associated with the connection. I’m skipping those parameters list over here.
7. Reference
visit ssl.com and wiki: TLS protocol.
I hope you enjoyed this post about 4 phases of SSL protocol and its phases in details, visit Linux tutorial for more details.
You have reached this point, which means you like this post, you are requested to comment to improve this post. Happy Learning 🙂