SSH protocol is a secure protocol for secure remote login. It is a widely used remote login protocol to login from one Linux/UNIX system to another Linux/UNIX system login.
1. ssh protocol overview
SSH is a remote login and remote login is a client-server program and protocol that provides an interactive command-line interface to a remote computer, using a protocol over the computer.
It allows a user to establish a secure channel over an insecure network in a client-server architecture, connecting an SSH client application with an SSH Server.
syntax of ssh command as follows:
ssh userName@remoteServerIp ssh -i mysoftkey.pem ec2-user@13.126.1.7
for getting help or getting different options:
ssh --help
syntax of remote login via ssh: from one linux server to another
There are two different approaches to remote login in Linux/Unix:
- by using sshKey
- by using without sshKey ( using password)
$ ssh userName@remoteServerIp ## via sshKey, sshKeyFileName must be in the local machine $ ssh -i@ ## for example $ ssh -i mysoftkey.pem ec2-user@13.126.12.17
here, $ represents terminal, ssh utility must be installed in the client on server in order to use handshake and establishing of session and connection.
remote login by using username and password:
$ ssh ranjeet@20.19.14.242 ranjeet@20.19.14.242's password: Last login: Fri Jan 26 13:36:08 2018 from 122.161.167.96 [mysotkey@centos ~]$
remote login by using sshKey
PBMAC049:~ ranjeetjha$ ssh -i mysoftkey.pem ec2-user@13.126.12.17
Last login: Thu Jan 25 12:30:35 2018 from 10.1.10.64
__| __|_ )
_| ( / Amazon Linux AMI
___|\___|___|
https://aws.amazon.com/amazon-linux-ami/2017.03-release-notes/
13 package(s) needed for security, out of 49 available
Run "sudo yum update" to apply all updates.
Amazon Linux version 2017.09 is available.
[ec2-user@ip-10-80-1-32 ~]$
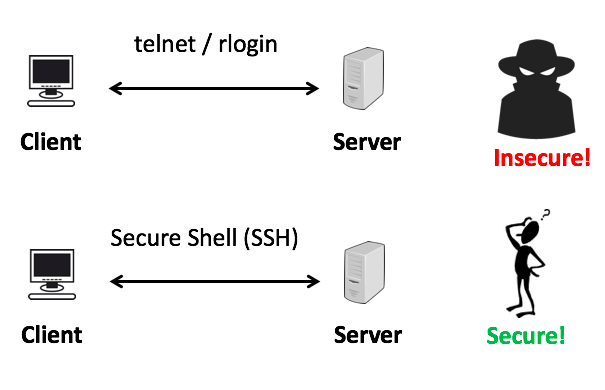
2. telnet or rlogin insecure
telnet or rlogin are the insecure protocol, no encryption and security involves during transmitting of data.
Any data that is being exchanged can be stolen from the communication path because in the telnet and rlogin no cryptographic procedures are applied.
SSH allows the run of the command insecure manner and cryptographic procedures are applied to transfer the data from client to server.
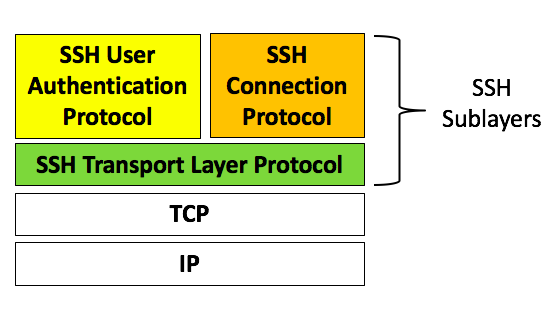
3. SSH sub-layers in transport Protocol
SSH is organised as three protocols:
- Transport Layer Protocol: it provides the followings:
- Server authentication
- data Confidentiality
- Data Integrity
- Compression ( optional)
- User Authentication Protocol: it authenticate users to the server.
- Connection Protocol: multiplexes multiple logical channels over a single underlying SSH connection.
These SSH sub-layers run on typically on top of TCP/IP.
4. Step by step SSH Authentication
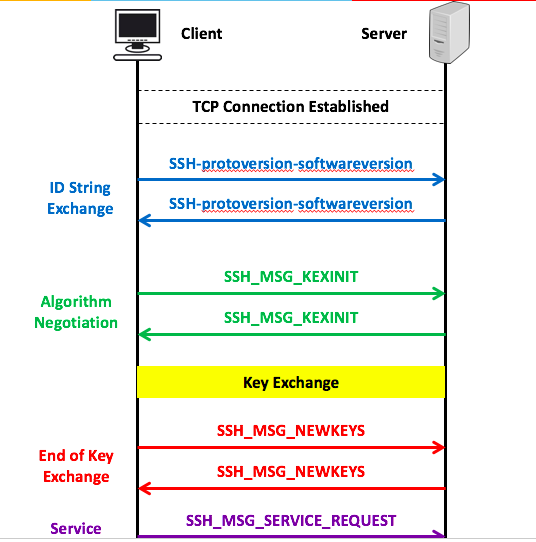
1. TCP connection: Once the TCP connection established the client and server exchange ID string.
2. Algorithm Negotiation: list of key messages exchange, with a list of the algorithm, key, and compression algorithm exchanges in this step.
3. key Exchange: in this step, the server is authenticated to the client, and server message authentication and the key will be generated.
4. End of key Exchange: It is an indication that each side can start sending messages by encryption and compression algorithm.
5. SSH User Authentication Protocol
SSH User Authentication Protocol allows the server to authenticate the client on one or more levels depending on the need for security.
There are different types of authentication methods, which are as follows:
- Password: The client sends a message containing a plaintext password, which is protected by encryption by the Transport Layer Protocol.
- Public Key: The client sends a message to the server that contains the client’s public key signed by the client’s private key. When the server receives this message, it checks whether the supplied key is acceptable for authentication and, if so, it checks whether the signature is correct.
- Host Based: Authentication is performed on the client’s host rather than the client itself. Thus, a host that supports multiple clients would provide authentication for all its clients. This method works by having the client send a signature created with the private key of the client host. Thus, rather than directly verifying the user’s identity, the SSH server verifies the identity of the client host.
6. ssh protocol: Different Channel Types
SSH Connection Protocol allows multiple channels to be opened up with the server through negotiation.
- session: The remote execution of a program. The program may be a shell, an application such as file transfer or e-mail, a system command, or some built-in subsystem. Once a session channel is opened, subsequent requests are used to start the remote program.
- x11: This refers to the X Window System, a computer software system and network protocol that provides a graphical user interface (GUI) for networked computers. X allows applications to run on a network server but to be displayed on a desktop machine.
- Forwarded-tcpip: This is remote port forwarding.
- direct-tcpip: This is local port forwarding.
Your comments are welcome to improve this post. Happy learning 🙂